Data Security for Manufacturing, Engineering, and the Supply Chain
Virtru helps manufacturers secure external communications and maintain compliance by enabling private data sharing workflows with industry-leading ease of use.
More Than 7,000 Customers Trust Virtru for Data Security and Privacy Protection


Modernize Supply Chain Communications with True Data Security
Manufacturing companies create and store an increasing amount of sensitive data in the cloud. To maintain a competitive advantage and meet compliance standards for government contracts, manufacturers must protect their data as it’s shared throughout the supply chain.
Virtru gives manufacturing companies persistent protection and granular controls to maintain the privacy of their IP, wherever it is shared. Because Virtru is certified Authorized to Operate (ATO) at the moderate level under FedRAMP, we adhere to the security controls defined in the NIST 800-53 and 800-171 publications to ensure the integrity of federal information systems. This means Virtru can:
- Help manufacturers continuously comply with NIST 800-171 guidelines
- Prevent unauthorized access to sensitive data
- Enable digital sharing workflows in a cloud environment
Security and Ease of Use to Transform Supply Chain Operations
True Privacy
Ensure no unauthorized third party ever has access to your data, no matter where it’s shared.
Ease of Use
Enable broad adoption with seamless user experiences, embedded where users, admins and partners already work.
Innovate with Confidence
Don’t let dynamic data protection and regulatory requirements slow down software development and IT projects.
Keep Proprietary Data Private, Wherever It Is Shared
Ensure True Privacy for Your Customers
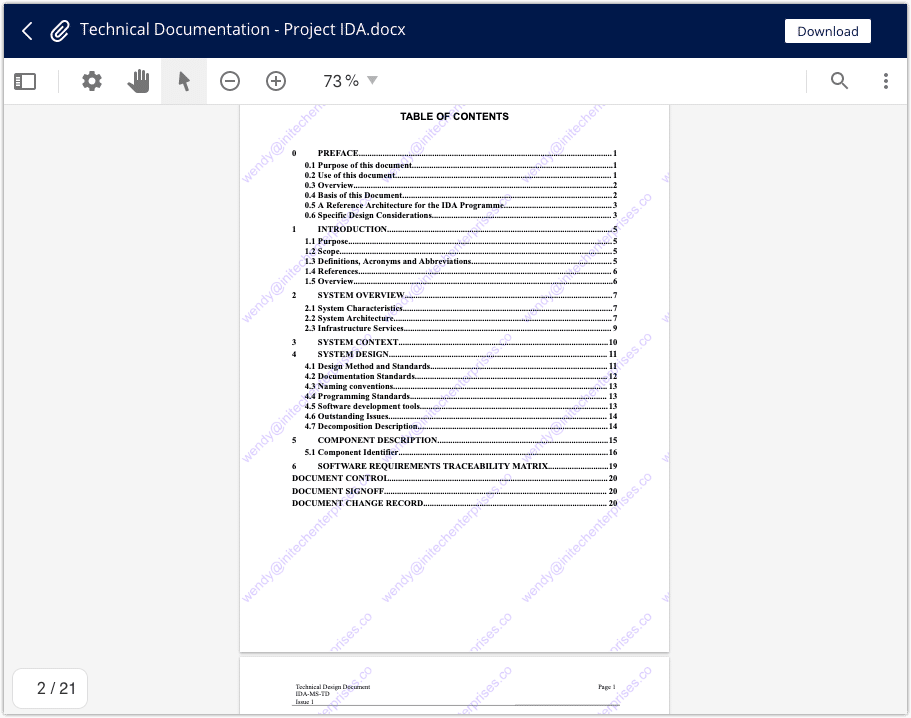
Encrypt emails, CAD documents, or any other file type containing proprietary R&D information, product specifications, industrial designs, and other intellectual property.
Host your own encryption keys to keep data private and prevent government surveillance.
.png?width=1337&height=1267&name=Simplified-Screenshots_Microsoft-highlight-dropshadow%20(1).png)
Seamless and Secure Sharing to Power Continuous Innovation
Give employees and administrators easy-to-use data protection, embedded in existing applications, such as Gmail, Outlook, and Google Drive.
Avoid complexities of S/MIME with transparent key exchanges that enable easy, secure data sharing with suppliers and reduced overhead for administrators.
Enable seamless access for suppliers, without requiring new accounts, passwords, or software, for digital sharing workflows that support rapid product development cycles.
Granular Access Control and Audit
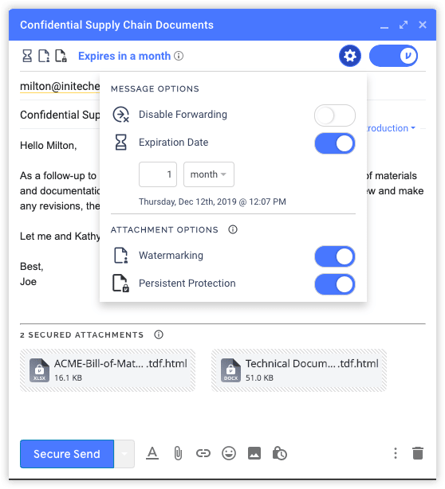
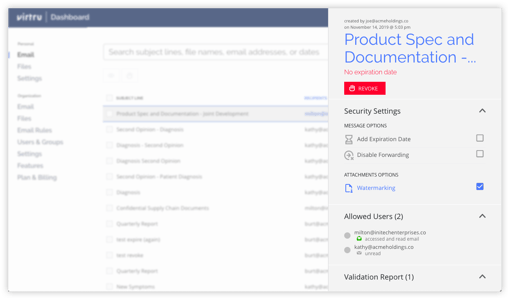
Control proprietary data wherever it’s shared with instant access revocation, expiration, disable forwarding, and document watermarking.
Audit who has accessed your data, when, where, and for how long. Integrate with your SIEM to flag unusual activity.
Securely Exchange Files with Anyone
Easily send, receive, manage, and protect the data you need across various partners, vendors, and customers, including:
- Requesting sensitive product information from customers
- Gathering data from logistical supply chain partners
- Requesting proposals from supply chain partners for particular projects