Granular Data Security and Access Control for Threat Intelligence
Threat intelligence companies are at the tip of the spear, proactively seeking out vulnerabilities and uncovering cyber attacks. Virtru helps these organizations collaborate securely and confidently.
Secure, Compliant File Sharing for Threat Intelligence Teams
Whether it's exchanging large files or sending quick, controlled email communications, Virtru helps Threat Intel teams conduct sensitive research easily and securely.

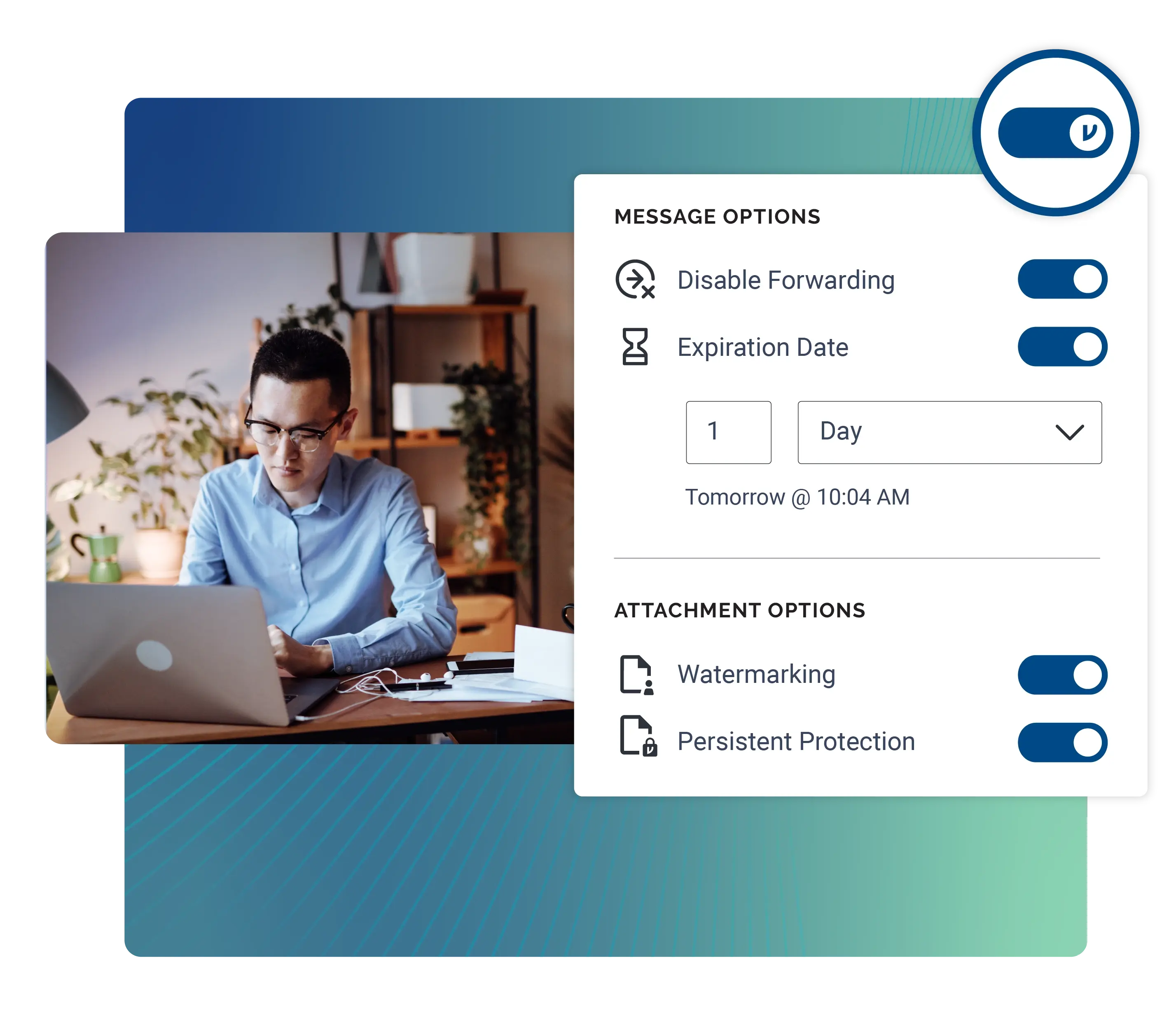
/Virtru%20Watermarking%20Outlook.webp)



/Virtru%20Watermarking%20Outlook.webp)
Why Threat Intel CISOs Use Virtru
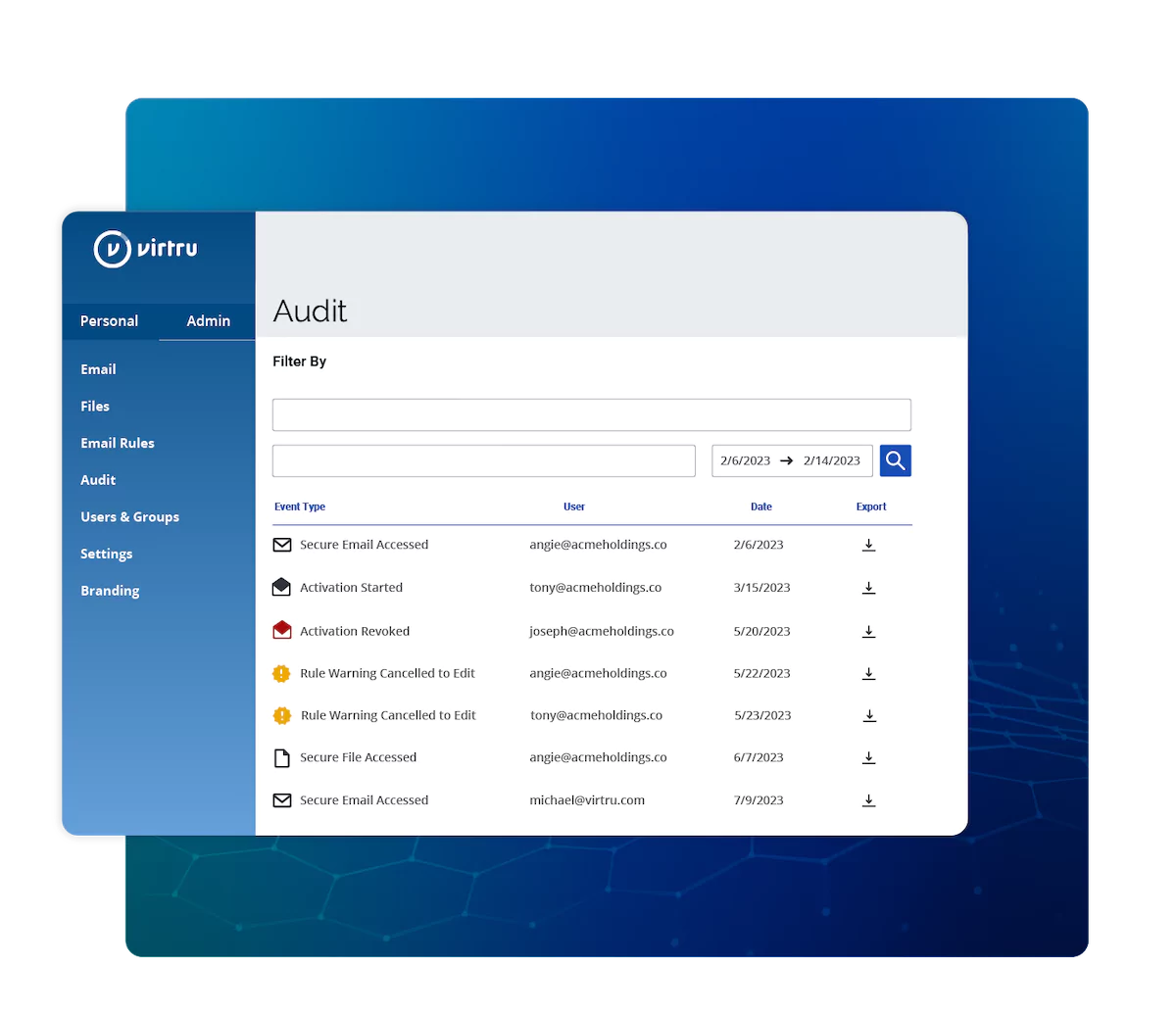
/Virtru%20DSP%20FedRamp.webp)
FedRAMP Authorized, FIPS 140-2 Validated Data Security Platform
Built on the open Trusted Data Format, the Virtru Data Security Platform underpins all of Virtru's products, providing FedRAMP authorized, FIPS validated protection that supports the world's strictest compliance standards.
Learn MoreEasy-to-Use, Fast-to-Deploy Data Security
Hear directly from Roderick Chambers, Senior Security and Risk Engineer at Recorded Future, on why their threat intelligence company leverages Virtru for encrypted email and file sharing in the Google Workspace ecosystem.
Learn More/Copy%20of%20DSP-TDF.webp)
Strengthen CMMC Compliance and Securely Manage CUI
Virtru is a trusted provider of data security solutions for CMMC compliance, supporting 27 of the 110 Level 2 controls outlined in CMMC 2.0. Virtru is an established partner to organizations throughout the Defense Industrial Base (DIB).
Learn More
Control Your Own Encryption Keys for Data Sovereignty
With the Virtru Private Keystore, you can maintain control of your own encryption keys, on-premises or in a virtual private cloud, for heightened privacy and control that separates your keys from your content.
Learn More

“When it comes to communicating with third-party partners, we believe frictionless collaboration holds the same level of importance as privacy, security, and compliance with governance controls.”
Dr. Dan Berrigan
Lead, Collaborative Tools, AFRL Digital War Room
Ready to take the next step?
Join the 6,700+ organizations that trust Virtru to protect highly sensitive information that needs to be shared.
6,100 CUSTOMERS TRUST VIRTRU FOR DATA SECURITY AND PRIVACY PROTECTION.

/Master-Electronics%20copy.webp)

