Zero Trust Data Sharing for DoD Contractors
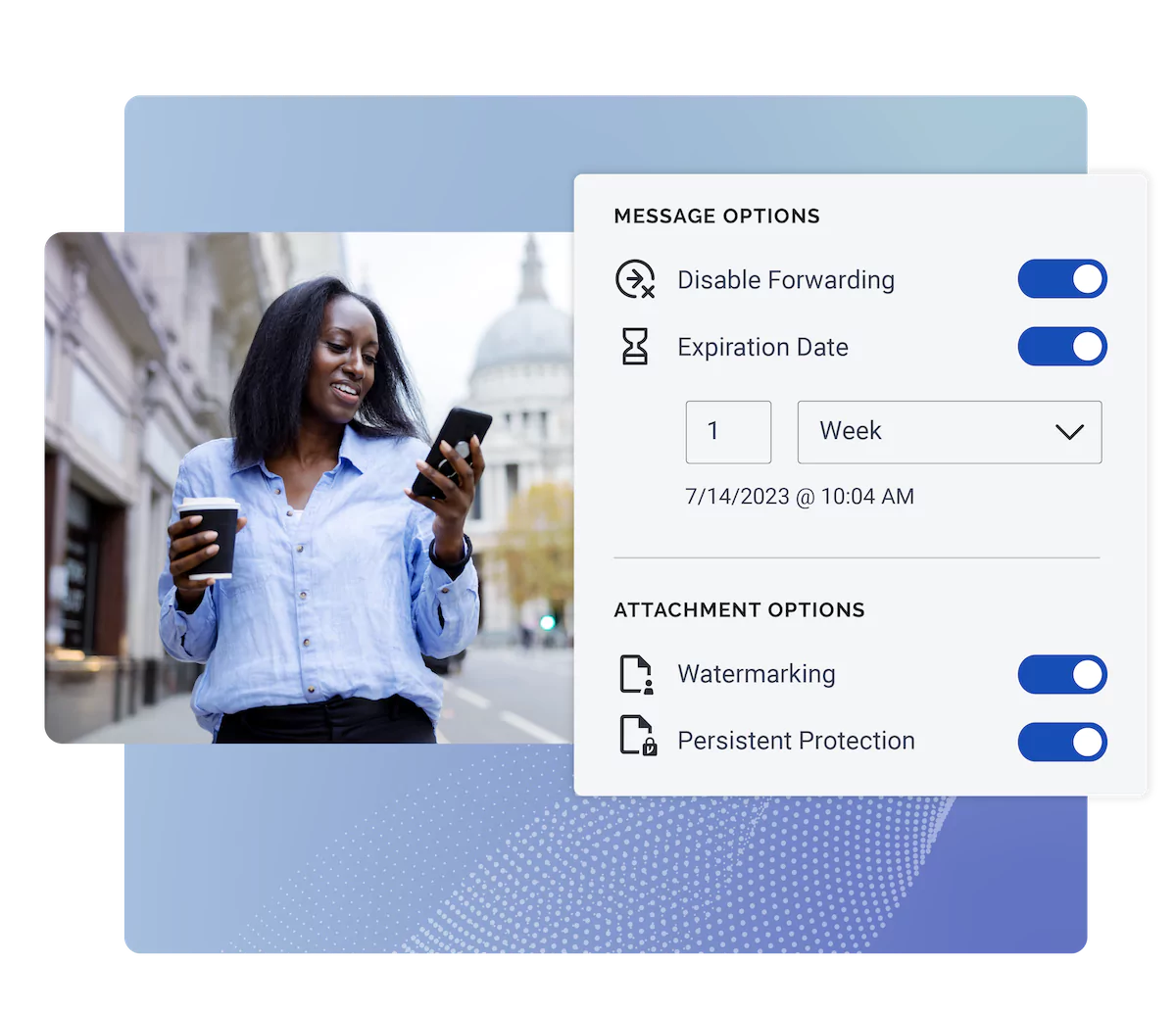
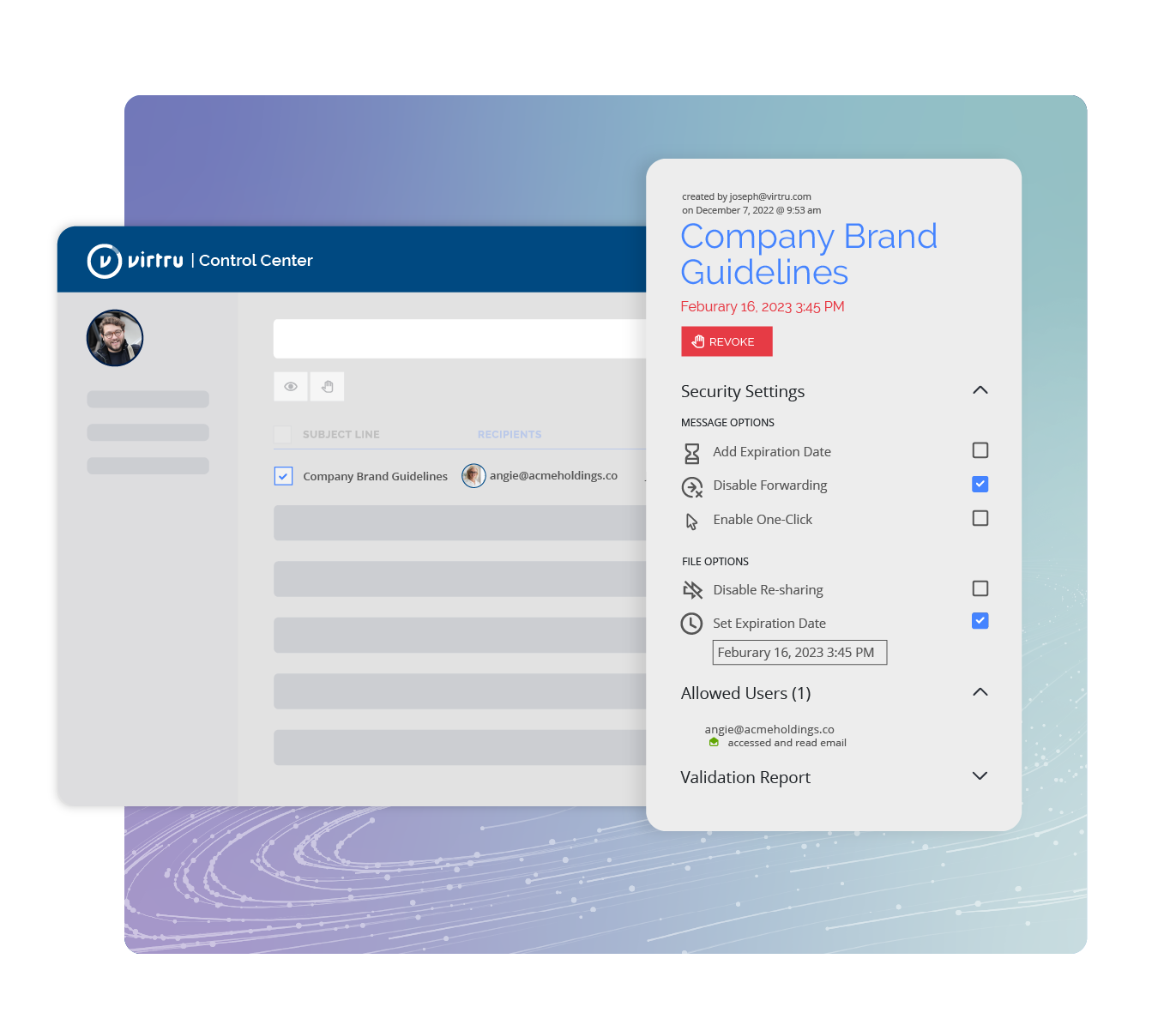
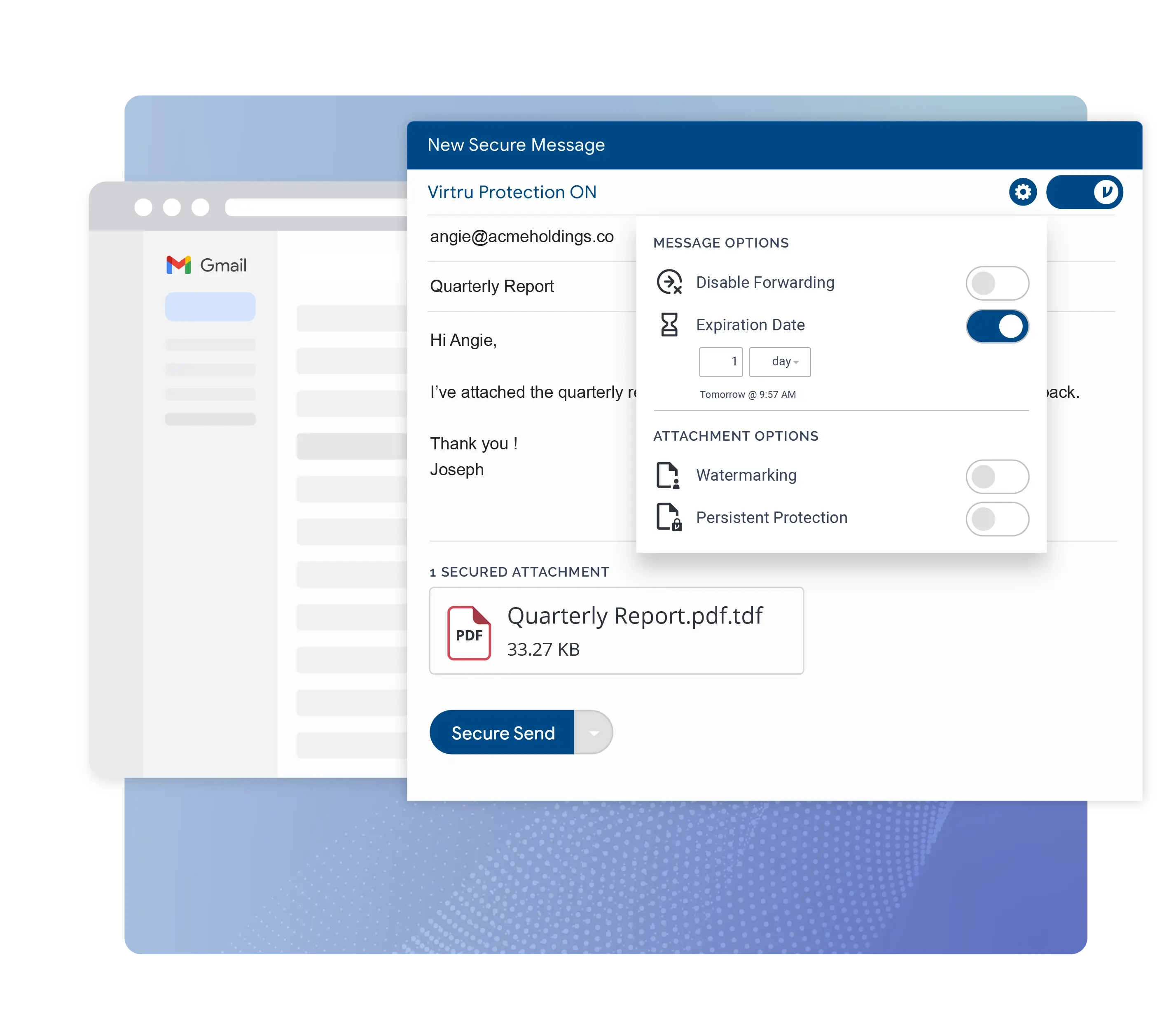
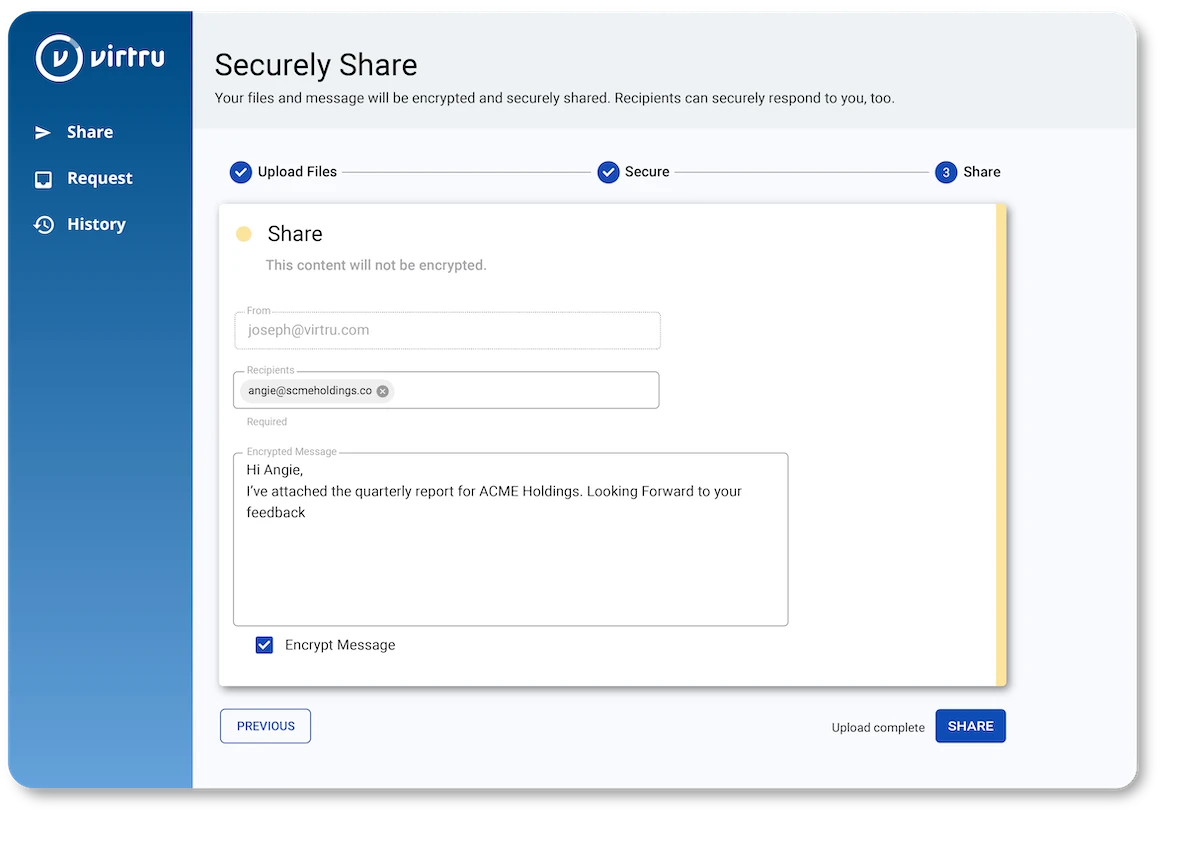
With Virtru, defense contractors can strengthen their Zero Trust postures aligned with the DoD Zero Trust architecture. The DoD highlights the data pillar as the central element of Zero Trust, and Virtru protects data in motion and at rest.