The Journey of An Unencrypted Email

So when you send an unencrypted email, how vulnerable are you, anyway? We’ve already written about the journey an encrypted email goes through, from composing a draft in your email client to landing in your recipient’s inbox. While the path looks a little different depending on what type of encryption you’re using, one thing’s for certain: using client-side email encryption helps lock down all the various opportunities a hacker has to access your data.
The number of stops your email makes after it leaves your inbox may surprise you, so let’s peel back the layers and see what happens when you send an unencrypted email — and, from a hacker or cyberspy’s point of view, how many places you can intercept that email and steal the content.
Unencrypted Email: What Can Go Wrong
“The journey of an unencrypted email really is the inverse of the journey of an encrypted email. Every little step of the way, you have attack vectors that might simply not be an issue if you had sent an encrypted email,” says Will Ackerly, Co-Founder and Chief Technology Officer of Virtru.
It’s easy to think about email as a direct journey from point A (the sender’s computer) to point B (the recipient or recipients’ computers). But even before an unencrypted email leaves your inbox, it poses a threat to your data security and privacy — and once it does leave, it passes through a few pit stops before reaching its final destination.
“There are three hops every email goes through on its way to a recipient,” says Ackerly. “With each hop there may or may not be an encrypted connection, and the only one you can be sure of is that first hop (if you’re using webmail client like Gmail, which uses SSL/TLS to encrypt email.)”
1. Stop one: your email server.
“If I’m sending an email with Gmail, there’s a connection from me to Google,” says Ackerly. “That’s the first hop, and you can tell if that connection is encrypted. All you have to do is look in your address bar for that green lock.”
2. Stop two: your recipient’s email server.
Then, Google communicates with, say, Yahoo (if I’m sending email to to a Yahoo user),” says Ackerly. “That’s the second hop.” And that’s the second place your email can be intercepted, if your recipient’s mail client doesn’t use email encryption.
“This second hop is where end users have no visibility into the process,” says Ackerly. “It’s almost impossible to tell if the connection between your email provider and your recipient’s email provider is encrypted or not. Google can do all they want to encrypt Gmail, but if your recipient’s provider doesn’t support an encrypted connection, Google has no choice but to let it out in cleartext. And that’s the default email state, actually. It’s unprotected and readable to anyone who gets a hold of that message.”
3. Stop three: your recipient’s computer.
“Finally, the email goes from Yahoo proper to your recipient, and that’s the third hop,” says Ackerly, “and it’s another place your email can be compromised.” Once your recipient opens up the email, they can forward it to whomever they please, creating a chain of vulnerable points.
“That’s the life of an unencrypted email,” says Ackerly. “It might, as with Gmail, be encrypted from one hop to another, but in the other hops it may exist in an unprotected state. And if any of those four entities linked by those three hops makes a mistake, your data can be compromised.”
With so many potential places your unencrypted email can be thwarted, either by hackers who want to steal your data, cyberthieves after your intellectual property or simply someone snooping, the prospect of not protecting your email messages and attachments looks pretty frightening.
And for every business that corresponded with Sony Pictures around the time of their 2014 hack, that fear became a little too real.
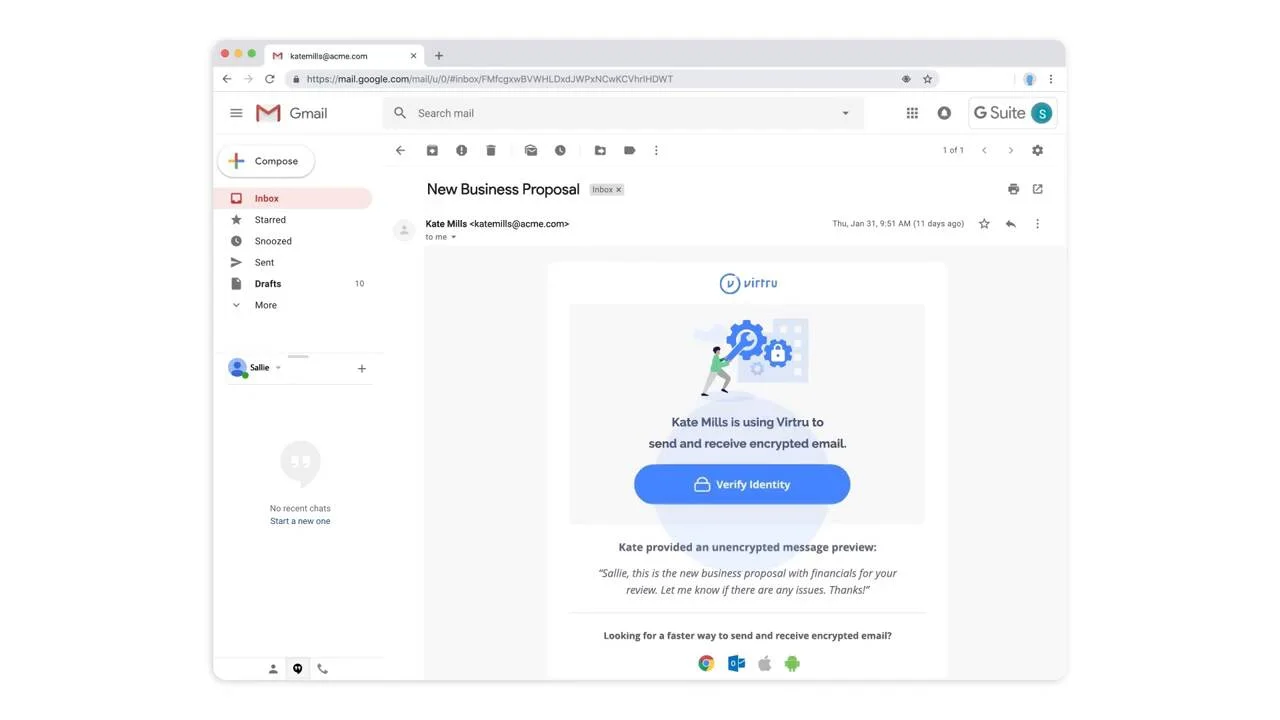
Your Email’s Destination Could Be Your Main Point of Weakness
“Something I think was really unintuitive until the Sony hack is that the biggest threat to enterprise email security is what happens to the email on the recipient’s end,” says Ackerly. “That includes both the recipient’s computer and the recipient enterprise, if you’re sending an email to another enterprise system.”
Sony’s lax privacy and security habits leading up to the infamous hack didn’t just put Sony in danger — Snapchat also ended up in the hackers’ crosshairs, by virtue of having exchanged unencrypted email with Sony.
“The Sony Hack really put a spotlight on the vulnerability of your email’s destination. The CEO of Snapchat was sending email to an advisor at Sony, and when Sony’s email servers were hacked, it put everyone they had exchanged unencrypted email with at risk,” says Ackerly. “And that included SnapChat.”
Some of those emails included private conversations between Snapchat and Sony Entertainment CEO Michael Lynton, who also serves as a Snapchat board member, detailing Snapchat’s business ambitions. Plans to expand into new markets, secret acquisitions and ideas for new features and functionality all leaked as a result of the Sony hack.
“This massive breach didn’t happen because anyone at SnapChat wasn’t doing a good job,” says Ackerly. “It’s because with unencrypted email, there’s just a great deal of inherent risk. There are several parties that have custodianship of the email that you send. You’re relying on them to do their due diligence to protect their content. If they mess up, you’re caught in the net.”
The vulnerability of your recipient’s computer, as well as their email server (whether hosted on premises, in the cloud or as part of a service like Gmail or Yahoo) could be your email security’s downfall — but your own device isn’t immune, either.
How Your Own Computer is a Threat To Your Email Security
One of the major concerns enterprises express when migrating their on-premises email solution (Exchange, for example) to the cloud is security. And Outlook, Apple Mail and other desktop clients are still very popular solutions for businesses. Isn’t there something inherently less secure about hosting your email in the cloud?
Not necessarily. For one, migrating to Gmail (via Google Apps for Work — now known as G Suite) as your enterprise email solution means that you’re getting at least a little bit of protection via email encryption, as Google bakes SSL/TLS encryption into its email product. It may be an incomplete solution compared to client-side encryption — and it won’t fly in the context of certain regulatory and compliance regimes, like HIPAA or CJIS — but it’s certainly better than nothing at all.
There’s also the issue of your computer. If you’re using a desktop email client, what happens if, say, your laptop is stolen?
“If you’re using webmail, particularly Gmail, you have a small amount of protection. You’re actually pretty safe in regards to creating sensitive data on your computer,” says Ackerly. “If your computer is stolen, and you use a desktop email client like Apple Mail, then all of those email messages — not just the ones you’ve sent, but also the ones you’ve received — are vulnerable to theft. They’re not protected or encrypted in any way.”
In that regard, using a webmail service like Gmail, which stores your data remotely on high-security servers, actually makes a lot of sense. “Additionally, desktop email programs often download your entire inbox, which might constitute a large chunk of either your private or your corporate/professional life, to your device.”
Unless your computer is encrypted, that can result in costly breaches. “There have been examples of where a single doctor publishes the data from one computer on the Internet, usually by mistake, and it results in millions and millions of dollars in HIPAA violation penalties and other costs. That can happen with desktop email, as well,” says Ackerly. “But with webmail clients like Gmail, when you create a draft or send out an email, you’re not creating a copy on your computer that can then be lost or leaked. There are still many copies that can be breached — once you create a draft, that content now persists on a backend server — but you won’t necessarily have a copy on your device that can be leaked or ‘lost.’”
The Menace of User Error (And Importance of Data Loss Protection)
But hacking, surveillance/espionage and laptop theft aren’t the only reasons it’s unsafe to send unencrypted email. A lot of times, the greatest enemy of your organization’s email privacy and security is your organization itself.
“One of the biggest actual threats in enterprise email security is simply user error,” says Ackerly. “We talk a lot about the ‘conscious actor,’ whether that’s a malicious insider or an outside hacker, posing a threat, but a ton of security incidents are due to mistakes.”
That mistake could be could be typing the wrong person’s address in the “To” line. It could be forwarding an email without realizing that there is sensitive data buried at the bottom of the chain, below the relevant email you wanted to forward. The ability to detect that and react to it is crucial to preventing major email security incidents in the enterprise.
“This speaks to the importance of Data Loss Protection (DLP), and why Virtru includes DLP in its email encryption solution,” says Ackerly. “The email admin can say ahead of time, ‘These are the words that will cause us a security issue if we include them in email.’ Beyond the obvious, like the words ‘top secret’ or ‘for your eyes only,’ there are also patterns the software looks for in your email before you send it.”
For example, if your email contains a number typed in the Social Security Number pattern (xxx-xx-xxxx), or a 16-digit number that looks like a credit card number, Virtru will actually highlight it when you hit “Send,” and then ask if you want to send the message as an encrypted email.
“This constitutes the Virtru extension intelligently scanning your content for these potential security risks, but this all happens in your plugin — no third party actually has access to your content.,” explains Ackerly. “The feature is sort of like a spell check function, but for data loss. The concept of looking for very sensitive data, and then enforcing the policy, is a capability very few companies have right now, because the data is being stored on a server somewhere. But the ability to enforce these DLP protections is something we’ve seen a lot of enterprise start asking for.”
With DLP, you’re no longer relying on the user to know whether or not to encrypt, and preventing a lot of the ‘oops’ moments that can lead to data breaches.
What Happens to Encrypted Email Sent With Portal Systems
While unencrypted email passes through the three hops of an email’s journey unprotected, what if you’re using a portal system to send encrypted email? You’re still getting a limited kind of protection, explains Ackerly. “The portal stores an unencrypted version of the email. A lot of companies call these portal systems ‘encrypted email,’ but the reality is that it’s truly no more encrypted than an email encrypted with SSL/TLS (like Gmail).”
Which means your email isn’t secure over every hop. “That email provider will hold onto the email and only allow the unencrypted content to go over an encrypted point-to-point connection to the recipient. Really what you’re buying there is a guarantee that the last hop is over a point-to-point encrypted connection.”
Also, enterprises do give up some ownership of their own email content when they choose a portal solution. “Here’s the tradeoff: you’re giving up another unencrypted version of your email to another provider. Instead of Google getting the email and sending it off, you’re giving it to the portal provider,” says Ackerly. “The downside is that they can see the content — unlike with client-side email encryption, those portal providers have access to the underlying data.”
For true protection across every stop your email goes through, as well as full privacy ownership of your organization’s content, you need a client-side email encryption service like Virtru.
Virtru: Client-Side Encryption & DLP to Protect Your Email Every Step of the Way
It’s clear that the journey an email goes through, from draft to your recipient’s inbox (and beyond), looks much different depending on whether you use no encryption, limited encryption (as with SSL/TLS or portals) or client-side email encryption.
Virtru Pro not only provides client-side email encryption and data loss protection to keep your encrypted email secure and private from start to finish, but it gives you granular control over your inbox. With forwarding control, you can make sure that your intended recipient is the only recipient of the email you send. With email recall, you can take back a message you might have sent by mistake. You can also set expiration dates on your email.
Virtru works seamlessly with the webmail provider you already use to protect your messages and attachments, all with the simple flick of a switch. Take ownership of your data today and download Virtru to send encrypted email.

Editorial Team
The editorial team consists of Virtru brand experts, content editors, and vetted field authorities. We ensure quality, accuracy, and integrity through robust editorial oversight, review, and optimization of content from trusted sources, including use of generative AI tools.
View more posts by Editorial TeamSee Virtru In Action
Sign Up for the Virtru Newsletter