How to Encrypt Email in Microsoft Outlook

Microsoft Outlook has been a cornerstone of the business world for decades. It’s the primary productivity app that thousands of organizations use to send emails, plan meetings, and share files. As security challenges continue to mount, it’s essential to implement the best protection for the platform itself and all emails within Outlook.
Encryption remains the industry standard for data protection, and it comes in a variety of forms and services. Microsoft offers several built-in encryption options, each with its own costs, benefits, and potential downsides. Third-party providers like Virtru supplement those options with easy encryption services that integrate directly into Outlook.
Outlook’s Native Encryption Options
Microsoft provides a wide variety of options for encrypting your Outlook emails, and those options vary depending on your organization's package. However, many of them aren’t particularly user-friendly — and they could still leave gaps in your email protection. And if you're looking at strict compliance regulations like CMMC 2.0 and ITAR, you'll be paying a hefty fee for encryption that meets those standards. (For example, one of our customers, a large global engineering firm, saved over $1M by choosing Virtru encryption vs. Microsoft GCC High.)
It's also important to understand who owns your encryption keys: When it comes to Microsoft encryption, many customers are in the position of trusting both their content and their encryption keys to Microsoft, when it would be much more powerful and secure for customers to host their keys independently of their content to reduce the potential of a breach.
Those gaps aren’t just a security risk. They’re a serious problem for businesses that need to comply with any data protection regulations like CMMC, ITAR, and CJIS. The majority of security regulations require persistent data protection, and incomplete protection options don’t offer enough security.
TLS Encryption
Transport-layer security (TLS) is the current standard of protection for email servers. All large platforms provide TLS encryption, which protects your emails within the network or while in transit. Outlook transmits any messages you send through an encrypted channel, preventing any eavesdroppers; it also encrypts the server your emails are hosted on.
Think of TLS like a bunker system. Your server is a bunker with strong walls. When you send an email, it goes through a protected underground tunnel right to another bunker (the recipient’s server). Emails at rest and in transit are fully protected by a perimeter of encryption.
The great thing is, you don’t need to do anything to set this up — it’s included in Outlook by default. However, it’s not a complete solution — especially if you're beholden to stricter compliance regulations. TLS doesn’t affect anything within that bunker system: your emails themselves are still just plain text. If an enemy enters the bunker, your emails are unprotected.
And, as we have seen by the ever-escalating sophistication and frequency of cyber attacks, it's not a question of "if," but "when" the enemy gains access the bunker.
Office 365 Message Encryption (OME): Now Deprecated
Historically, Microsoft offered OME, which allows you to encrypt text within emails. This native feature had significant drawbacks: depending on the version of Outlook, setup could be complicated and time-consuming, and encryption functionalities were only optimized for certain Outlook recipients.
Notably, in 2023, security researchers identified what they considered a significant OME security vulnerability, wherein a bad actor could unlock encrypted information given a large enough volume of content to work with. Also in 2023, Microsoft deprecated OME in favor of Microsoft Purview Message Encryption.
Microsoft Purview Message Encryption
Microsoft Purview Message Encryption is available to users on certain Microsoft SKUs. To encrypt email messages with Purview, just click the “Encrypt” button and select the rules you want to enforce. You can also dig through your settings to encrypt all outgoing messages by default. This encrypts your email’s text and all its attachments.
Sounds easy, right? Unfortunately, it’s not that straightforward. There are three critical issues:
1. An admin will need to define transport rules to determine how a message is encrypted.
Microsoft’s screenshot is deceiving here. The only default options are “Encrypt” and “Do Not Forward.” If you need to customize any rules, an admin will need to go through a hefty setup process and configure encryption settings for that rule.
Moreover, automatic encryption rules are only enforced after Microsoft has read your unencrypted message to see if the content meets any of those rules, so your email content is fully visible to Microsoft.
2. Purview is easy–if both the sender and the user have the right applications to support that encryption.
Outlook’s encryption works best with other Outlook servers. If your recipients use Outlook 365 or certain newer versions of Outlook for PC, they’ll be able to open the encrypted message normally. Any other platform (including other Outlook options) is more complicated.
OME can work with Gmail and other standard clients, but in a time-consuming and fractured way. Recipients are redirected to an Outlook web page to sign in or request a one-time password in order to read messages in a browser window.
3. Setup varies wildly across different Outlook versions and subscriptions.
Microsoft’s setup page for Outlook encryption is pretty hard to follow because it outlines both S/MIME and 365 Message Encryption "flavors" of Microsoft encryption. It’s not particularly user-friendly or consistent.
In some cases, you can simply click the Encrypt button. In others, you’ll see a permissions button. You may see an options tab, which leads to more options, which has a dialogue box launcher, which leads to security settings, where you can select the encryption option… for a single message.
Even then, some recipients may need a key to open messages: “Only the recipient who has the private key that matches the public key used to encrypt the message can decipher the message for reading.”
Office 365 Message Encryption definitely improves the security of your emails. But, it also adds significantly to the workload required to secure those emails.
S/MIME for Outlook and Legacy Systems
Outlook also supports S/MIME encryption, which is an older encryption format. However, it’s not a superior option: S/MIME has all of the downsides of Purview and then some.
First of all, you need to install a special certificate before you can use S/MIME in Outlook. Second, both the sender and the recipient need to have S/MIME encryption standards configured on their mail application. If your email is going to someone without S/MIME set up, it simply won’t be readable for that person. Unfortunately, it’s not widely supported, so many recipients will be unable to set S/MIME up at all. Even if the message sends properly, you’ll need to give the recipient your encryption key to manually decode the email.
Third, S/MIME is vulnerable to outside attacks, like message takeovers; it also increases risk because users need to exchange encryption keys. If that key is compromised for any reason, your emails are no longer secure.
Other common encryption standards like PGP encryption have their own weaknesses and can be tricky to implement. Additionally, they’re not officially supported by Outlook, unlike S/MIME.
Azure Rights Management Services (RMS)
Azure RMS is another Microsoft security tool that protects your data with encryption, identity and authorization policies. This protection is data-centric, meaning stays with your data wherever it goes. Only authorized people or programs will be able to read your data (in this case, an email). If you have a technical background, you can also configure end-to-end encryption within RMS.
RMS is a powerful tool, but it’s cumbersome to set up and requires some technical expertise. Activation, bootstrapping (or initialization) and protection is a hefty process. For users without the time or background, or who simply want to secure their email effectively, RMS is not an optimal choice.
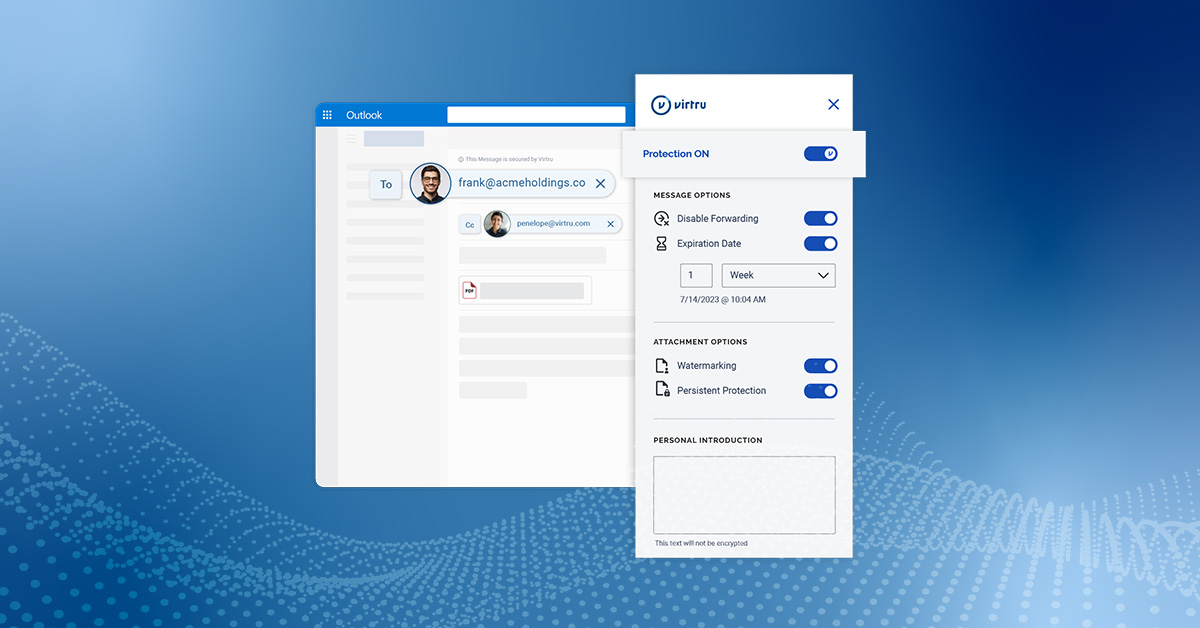
Encrypting Microsoft Email? Fill in the Gaps with Virtru.
Use Virtru to encrypt email in Microsoft Outlook for a superior user experience and military-grade security, with granular access control.
Our secure Outlook add-on integrate seamlessly with Outlook to provide easy, secure end-to-end encryption. With Virtru, you have full access control, including email expiration, revocation and instant access. Your encryption keys are stored separately from your encrypted emails, ensuring that only the right eyes see your content. You don’t need certificates, special software, a new account or one-time passwords–even if the recipient doesn’t use Virtru.
Best of all: it’s incredibly user-friendly and easy to set up. All your options and settings are visible right from your dashboard. You can even search through encrypted content. It’s the same usability you’re used to from Outlook, just with top-of-the-line security—and since usability is key to whether or not people actually use those security measures, that’s a pretty important feature.
Ready to explore Virtru’s encryption services for Outlook? Contact our team today for a demo.

Editorial Team
The editorial team consists of Virtru brand experts, content editors, and vetted field authorities. We ensure quality, accuracy, and integrity through robust editorial oversight, review, and optimization of content from trusted sources, including use of generative AI tools.
View more posts by Editorial TeamSee Virtru In Action
Sign Up for the Virtru Newsletter
/blog%20-%20Zero%20Trust%20Primer%20-%20N5K%20series/Zero-Trust-Primer%20copy.webp)
/blog%20-%20Private%20Cloud%20Compute%20is%20Only%20Half%20the%20Story/PrivateCloudCompute.png)



/blog%20-%20title%2048%20november%2010/cmmcnov10.webp)
/blog%20-%20ukraine%20and%20taiwan%20HIO%20recap/UkraineTaiwanRecapBlog.webp)
/blog%20-%20data%20liberation/data-liberation-2.jpg)
/blog%20-%20ACP-240%20and%20HIGHMAST/highmast-acp-240.webp)

/blog%20-%20discord-zendesk%20breach/discord-breach.webp)