NIST Compliant Data Protection for Intellectual Property
TABLE OF CONTENTS
See Virtru In Action


Manufacturers in the United States perform more than three-quarters of all private-sector R&D in the nation, driving more innovation than any other sector. Being the driving force for economic growth and innovation does not come without its challenges—protecting intellectual property (IP) and meeting NIST Cybersecurity Framework requirements are chief among them.
Securing Your IP
The first, protecting IP, cannot be overstated in terms of value—it is the lifeblood of any company. In fact, IP theft costs U.S. companies as much as $600 billion each year. When it comes to protecting proprietary information in the manufacturing industry, cybercrimes targeted at companies are designed to not only steal IP but cause physical disruption to operations and produce black-market replicas. Therefore, understanding what puts your organization at risk, and how to mitigate those risks is essential for data protection and security.
The supply chain is a massive threat vector.
Sharing data is essential for collaboration but the more service providers, contractors and third-party suppliers that come in contact with your IP, the more at-risk you become. Over the last year, 56% of organizations have had a breach that was caused by one of their vendors.
Legacy manufacturing infrastructures aren’t equipped to defend against modern attack methods.
Aging patchworks of vendors and equipment combined with perimeter-only security is an open invitation for cyberattackers.
Modernizing the supply chain with end-to-end encryption will ensure unauthorized parties—such as competitors or attackers—will not be able to access your proprietary data, like confidential R&D plans and product roadmap details.
Data Protection 101 with NIST 800-171
For manufacturers servicing the US government, protecting IP and sensitive data is not just a best practice, it is required for NIST 800-171 compliance.
The National Institute of Standards and Technology (NIST) is a non-regulatory government agency that provides a set of standards for recommended security controls for information systems to federal agencies. As such, the standards set forth by NIST are a critical resource for security among manufacturing companies that are a part of any government supply chain.
The main benefit of NIST compliance is that it helps to ensure an organization’s infrastructure is secure. Therefore, compliance with NIST guidelines—specifically NIST 800-171—has quickly become a top priority for organizations handling controlled unclassified information (CUI) such as emails, drawings, patents, personnel records, sales orders, or contracts. NIST 800-171 aims to help organizations that are a part of the government supply chain ensure that their systems that process CUI are secure and controlled. That means that a private sector firm—such as a hardware manufacturer that supplies the federal government— is subject to the requirements laid out in NIST 800-171.
How to Achieve NIST 800-171 Compliance
NIST 800-171 is comprised of 14 control families that establish guidelines for protecting CUI when stored and transmitted by non-federal systems and organizations:
- Access Control – Monitor all access events and limit access to systems and data.
- Awareness and Training – Ensure that managers and all users are aware of the security risks by providing security training on a regular basis.
- Audit and Accountability – Collect, analyze, and retain audit logs to detect unauthorized activity.
- Configuration Management – Establish and maintain baseline configurations and monitor user-installed software.
- Identification and Authentication – Verify the identity of all users and devices in your network by using multifactor authentication and upholding a strong password policy.
- Incident Response – Develop an incident response strategy and implement processes to detect, analyze, and respond to security incidents.
- Maintenance – Perform regular system maintenance.
- Media Protection – Ensure the security of both paper and digital media by limiting access and ensuring proper disposal.
- Physical Protection – Protect your hardware software, networks, and data from damage and loss by controlling physical access.
- Personnel Security – Monitor all user activities and protect systems that contain CUI.
- Risk Assessment – Regularly evaluate potential risks to your systems.
- Security Assessment – Monitor and assess its security controls to determine if they are effective enough and develop a plan to reduce security vulnerabilities in critical systems.
- System and Communications Protection – Prevent the unauthorized transfer of information by monitoring, controlling, and protecting information that is transmitted by your systems.
- System and Information Integrity – Identify and correct system flaws, and protect critical assets from malicious code.
NIST Privacy Framework
On September 9, NIST released the Preliminary Draft of the NIST Privacy Framework: A Tool for Improving Privacy through Enterprise Risk Management. Building on the widely adopted Cybersecurity Framework, the companion Privacy Framework will help organizations address the privacy risks and legal obligations associated with designing and deploying products and services. The Cybersecurity Framework has been critical in establishing a common lexicon for cybersecurity in government and industry as well and hopefully the final Privacy Framework can achieve this same goal.
As the convergence of privacy and security grows in response to public concern over the multitude of unauthorized data access incidents, NIST has been careful to honor the current cybersecurity guidance while adding privacy best practices to address the increasing need for data protection. NIST recognizes that cybersecurity risks arise from unauthorized activity while privacy risks are a byproduct of authorized data processing and that both play a role in a holistic data security strategy.
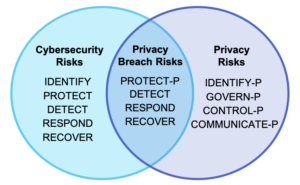
As the above Venn diagram illustrates, the application of the proposed Privacy Framework aims to address privacy risks associated with both data processing and privacy breaches. The Core functions of the Privacy Framework—Identify-P, Govern-P, Control-P, Communicate-P, and Protect-P, where the -P refers to privacy-focused activities—are designed to offer organizations flexibility when addressing privacy risks:
- Identify-P, Govern-P, Control-P and Communicate-P can be used to manage privacy risks that arise directly from data processing;
- Organizations can use Protect-P along with Detect, Respond and Recover from the Cybersecurity Framework to manage privacy risks arising from privacy breaches;
- Depending on the organization and the maturity of the security and privacy programs, organizations can also use all of the Cybersecurity Framework Functions alongside Identify-P, Govern-P, Control-P and Communicate-P to address risks that are both privacy and security related.
What does this mean for you?
NIST recognizes the importance of collaboration between privacy and security teams, and encourages organizations to view the proposed, voluntary framework with flexibility and apply it based on the maturity of the organization’s current privacy program. While some may use the framework as guidance for a new privacy program, others will see it as a means of identifying gaps in a current program. Ultimately the framework should serve as a guide for balancing innovative uses of data while minimizing negative consequences for employees, customers and partners.
How Can Virtru Help with NIST Compliance?
First things first, evaluate your current infrastructure to determine where you are currently NIST compliant and where you need to improve. Based on this gap analysis, you’ll see what changes you need to make and which features to look for in selecting a solution to help protect IP and CUI.
From the beginning, Virtru’s mission has been to protect privacy by securing data and helping organizations securely share data to achieve mission success. Modern data protection requires data-centric protection that persists with the data, including access controls and policy management. With end-to-end encryption, organizations can ensure sensitive data is protected at the object level, reducing your organization’s risk of IP theft, and helping to achieve NIST 800-171 compliance. As a FedRAMP authorized solution provider, Virtru can help you achieve data-centric protection and compliance goals, all while enabling an ecosystem that ensures secure data sharing and collaboration
Get in touch with us to learn more about how Virtru helps with NIST compliance and protecting your IP.
See Virtru In Action
Sign Up for the Virtru Newsletter